Search for person "Ilja"

46 min
Look what I found under the carpet
107 min
Breaking software in an automated fashion
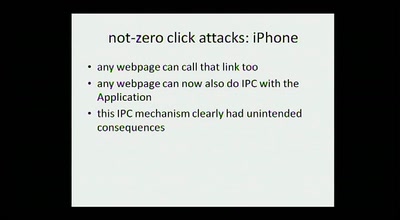
73 min
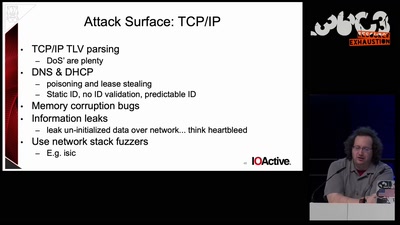
expanding the attack surface and then some
58 min
A survey of BSD kernel vulnerabilities.
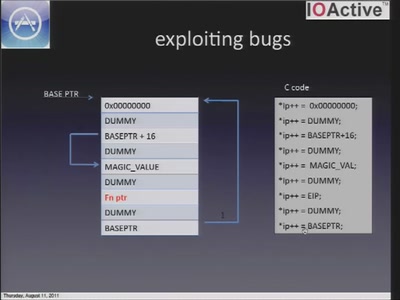
51 min
A look at the security of 3rd party iOS applications

61 min
why clearing memory is hard.
62 min
Auditing Boot Loaders by Example
