43 min
Hirne Hacken
Menschliche Faktoren der IT-Sicherheit

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
52 min
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

46 min
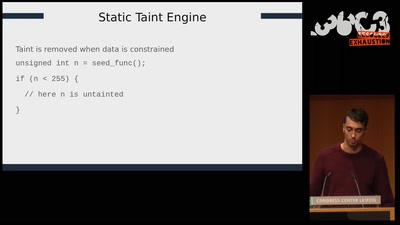
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

60 min
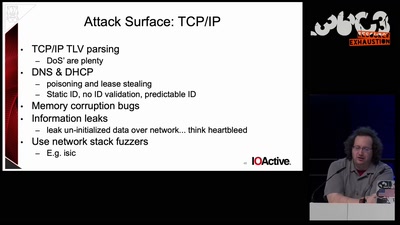
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
41 min
15 Jahre deutsche Telematikinfrastruktur (TI)
Die Realität beim Arztbesuch nach 15 Jahren Entwicklung…
61 min
Email authentication for penetration testers
When SPF is not enough

53 min
Cryptography demystified
An introduction without maths

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

46 min
It's not safe on the streets... especially for your 3DS!
Exploring a new attack surface on the 3DS

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

55 min
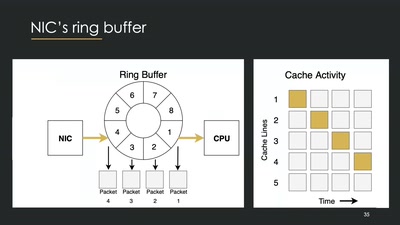
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

48 min