In this talk we will go through the different mitigations in Windows 10 and see how they affect modern userspace exploitation. We will explain the primary ones and the different ways to bypass them. Finally, we will demo a cool exploit that achieves code execution.
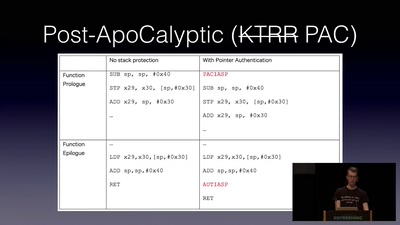
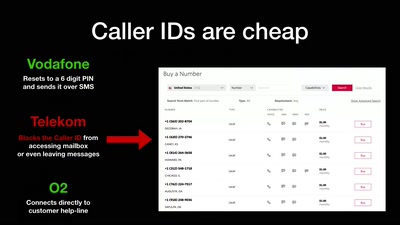
In the past few years, many new mitigation techniques were introduced both into Windows kernel and userspace. These are supposed to make exploitation of certain vulnerabilities significantly harder, reduce exploit reliability, and require dependency on multiple primitives. It impacts many of the core components of the OS and build stack, including the loader, front-end allocator, compiler, and memory management. With such investment and impact, how effective are these really, from the exploit developer’s perspective?
In this talk, we’ll explain the primary mitigations in Windows that hinder modern memory corruption exploitation in userspace. Using examples of real-world vulnerabilities, we will see how to achieve arbitrary code execution on different Windows versions, comparing their impact on exploits. On our journey to code execution, we will learn the motivation behind these mitigations, understand their design, scope, and implementation, and study their weaknesses.
Download
Video
These files contain multiple languages.
This Talk was translated into multiple languages. The files available for download contain all languages as separate audio-tracks. Most desktop video players allow you to choose between them.
Please look for "audio tracks" in your desktop video player.