Events for tag "24c3"
40 min
Introduction in MEMS
Skills for very small ninjas
57 min
Analysis of Sputnik Data from 23C3
Attempts to regenerate lost sequences

70 min
Der Bundestrojaner
Die Wahrheit haben wir auch nicht, aber gute Mythen
37 min
FeM-Streaming und Encoding
Abschlussbericht

52 min
I know who you clicked last summer
A swiss army knife for automatic social investigation

48 min
All Tomorrow's Condensation
A steampunk puppet extravaganza by monochrom and friends

38 min
Steam-Powered Telegraphy
A League of Telextraordinary Gentlemen present the marvel…
109 min
Hacker Jeopardy
Die ultimative Hacker-Quizshow

87 min
Chaos Jahresrückblick
Ein Überblick über die Aktivitäten des Clubs 2007
44 min
Unusual Web Bugs
A Web Hacker's Bag O' Tricks
48 min
One Token to Rule Them All
Post-Exploitation Fun in Windows Environments

60 min
EU Policy on RFID & Privacy
Developments 2007, Outlook 2008

44 min
Port Scanning improved
New ideas for old practices
58 min
The Arctic Cold War
The silent battle for claiming and controlling the Arctic

57 min
Spiel, Freude, Eierkuchen?
Die Gamerszene und ihre Reaktion auf kritische…

42 min
From Ring Zero to UID Zero
A couple of stories about kernel exploiting
50 min
To be or I2P
An introduction into anonymous communication with I2P
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007
63 min
Die Wahrheit und was wirklich passierte
Jede Geschichte hat vier Seiten.
70 min
Hacking in the age of declining everything
What can we do when everything we thought turns out to be…
51 min
After C: D, libd and the Slate project
A clean slate for operating systems

55 min
Getting Things Done
Der Antiverpeil-Talk

50 min
Design Noir
The seedy underbelly of electronic engineering

32 min
Absurde Mathematik
Paradoxa wider die mathematische Intuition

60 min
Data Retention and PNR
The Brussels Workshop

58 min
Meine Finger gehören mir
Die nächste Stufe der biometrischen Vollerfassung

57 min
Hacking SCADA
how to own critical infrastructures

50 min
Agenten des Bösen
Verschwörungstheorien

57 min
C64-DTV Hacking
Revisiting the legendary computer in a joystick

58 min
Cybercrime 2.0
Storm Worm

63 min
<NO>OOXML - A 12 euros campaign
Against Microsoft Office's broken standard

58 min
Digital Sustainability
Scarcity is Entering the Net
60 min
Open Source Lobbying, tips from the trenches
From one angry e-mail to writing national policy on open…

59 min
Simulating the Universe on Supercomputers
The evolution of cosmic structure

45 min
Toying with barcodes
Jemandem einen Strich auf die Rechnung machen

45 min
OpenSER SIP Server
VoIP-Systeme mit OpenSER

58 min
Hacking ICANN
tactics to hack the individual into the ICANN system

75 min
Tracker fahrn
We Track Harder - We Track More! Take the pain out of…
58 min
Linguistic Hacking
How to know what a text in an unknown language is about?

52 min
Lieber Cyborg als Göttin
Politischer Hacktivismus und Cyborgfeminismus
59 min
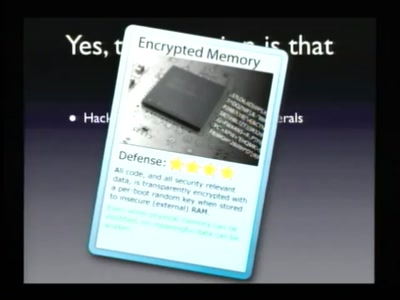
Why Silicon-Based Security is still that hard: Deconstructing Xbox 360 Security
Console Hacking 2007
62 min
Distributed campaigns for promoting and defending freedom in digital societies
Sharing experience about campaigning on the political field…
56 min
Hacking ideologies, part 2: Open Source, a capitalist movement
Free Software, Free Drugs and an ethics of death

34 min
Playstation Portable Cracking
How In The End We Got It All!

21 min
Space Communism
Communism or Space first?

42 min
Inside the Mac OS X Kernel
Debunking Mac OS Myths
59 min
It was a bad idea anyway...
The demise of electronic voting in The Netherlands
57 min
OpenStreetMap, the free Wiki world map
3 years done - 10 to go?

42 min
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

71 min
What is terrorism?
And who is terrorising whom?

54 min
Dining Cryptographers, The Protocol
Even slower than Tor and JAP together!

39 min
DIY Survival
How to survive the apocalypse or a robot uprising

59 min
Grundlagen der sicheren Programmierung
Typische Sicherheitslücken

52 min
23 Wege für Deine Rechte zu kämpfen
Wie man sich selbst mit den eigenen Stärken für unsere…

65 min
Elektronische Dokumente und die Zukunft des Lesens
Warum es so ewig gedauert hat, bis Bücher auf geeigneten…
65 min
Overtaking Proprietary Software Without Writing Code
"a few rough insights on sharpening free software"

56 min
Desperate House-Hackers
How to Hack the Pfandsystem

74 min
"I can count every star in the heavens above but I have no heart I can't fall in love…".
The image of computers in popular music
73 min
Das Panoptische Prinzip - Filme über die Zeit nach der Privatsphäre
Ergebnisse des Minutenfilmwettbewerbs des C4 und des Kölner…
60 min
Programming DNA
A 2-bit language for engineering biology

46 min
A collection of random things
Look what I found under the carpet
62 min
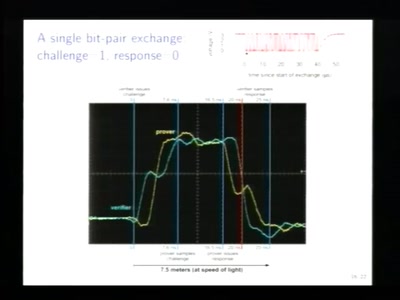
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close
90 min
Security Nightmares 2008
Oder: worüber wir nächstes Jahr lachen werden

59 min
10GE monitoring live!
How to find that special one out of millions

63 min
Wireless Kernel Tweaking
or how B.A.T.M.A.N. learned to fly

52 min
Modelling Infectious Diseases in Virtual Realities
The "corrupted blood" plague of WoW from an epidemiological…

33 min
Make Cool Things with Microcontrollers
Hacking with Microcontrollers

62 min