Search for person "Tom van Tilburg & Anne Blankert"
prev
next

55 min
The key elements of policy hacking
62 min
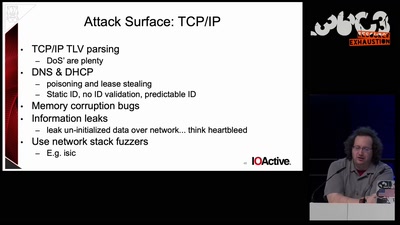
Auditing Boot Loaders by Example

45 min
Human-computer-synchronizations
51 min
Ein und Ausdrücke zum Thema (Gem)einsamkeit

60 min
How Betrusted Aims to Close the Hardware TOCTOU Gap

27 min
Keats, Wordsworth and Total Surveillance

60 min
Advanced Rowhammer exploitation on cloud, desktop, and…

45 min
Zur Performativität soziotechnischer Systeme und der…

53 min
NLNet sponsored (open hardware) trusted boot module
prev
next





