Search for person "Thorsten Schröder"
next
27 min
systemd soft-reboot and surviving it as application
How to leverage systemd soft-reboot in openSUSE
28 min
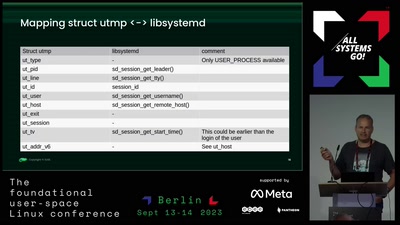
Y2038: utmp, wtmp and lastlog
How openSUSE solved this
60 min
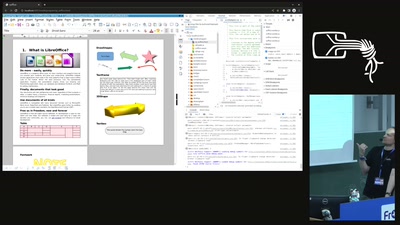
LOWA or how we managed to run LibreOffice in your browser (WASM edition)
Stories from the journey of porting a massive c++…
59 min
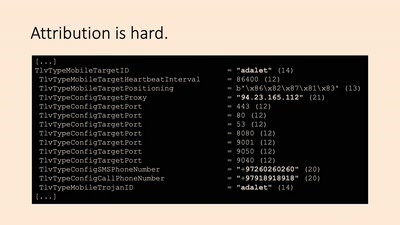
Finfisher verklagen
Rechtsbrüche beim Export von Überwachungssoftware
40 min
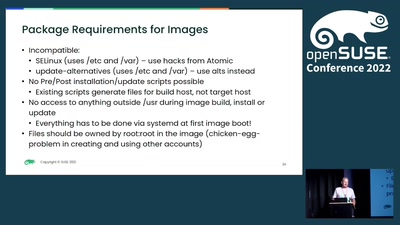
MicroOS TIU
Transactional Image Update
60 min
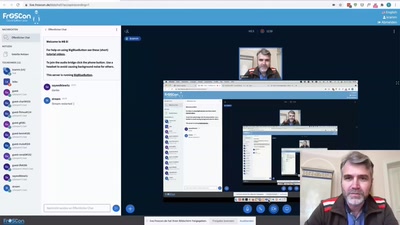
Komfortable und sichere Fernwartung für alle Betriebssysteme OSS
Mit RPort Linux, Windows und IoT sicher und komfortable…

57 min