Search for person "Marcel J. Dorsch"
prev
next

42 min
Creation and detection of IP steganography for covert…

62 min
Hot or Not: Defeating anonymity by monitoring clock skew to…
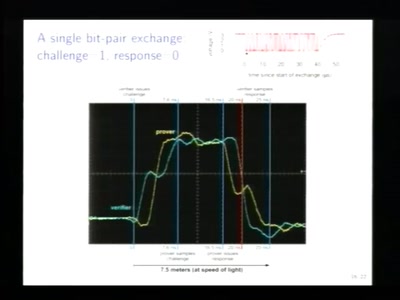
62 min
Keeping your enemies close
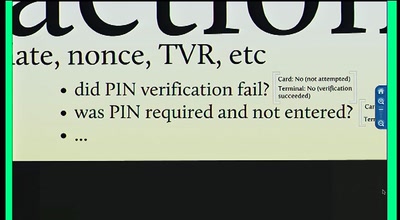
57 min
Vulnerabilities in the EMV Protocol
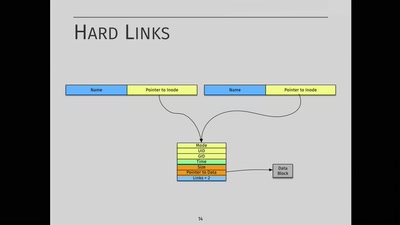
48 min
Von Inodes und Directories zu Indirection, Extents,…
prev
next



