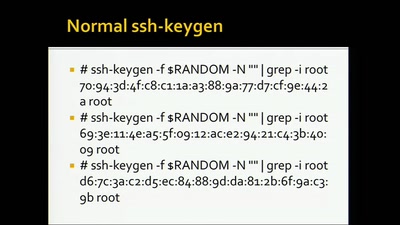
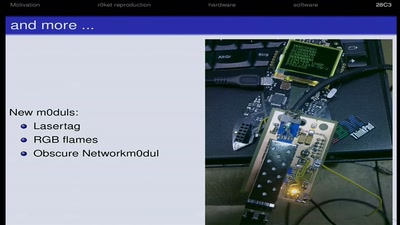
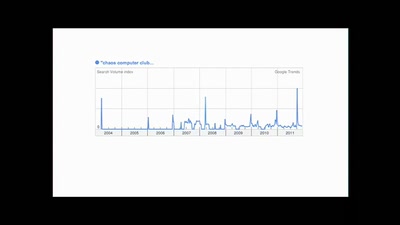
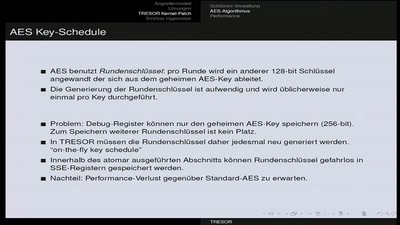
Events for tag "28c3"
45 min
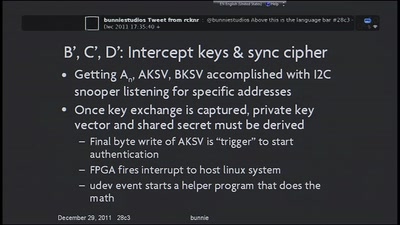
Implementation of MITM Attack on HDCP-Secured Links
A non-copyright circumventing application of the HDCP…

53 min
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..
45 min
Crowdsourcing Genome Wide Association Studies
Freeing Genetic Data from Corporate Vaults
57 min
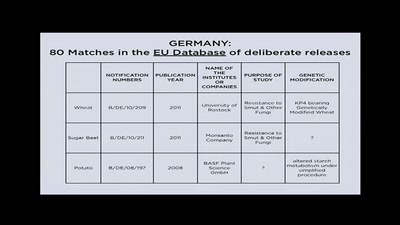
Eating in the Anthropocene
Transgenic Fish, Mutagenic Grapefruits and Space Potatoes

57 min
802.11 Packets in Packets
A Standard-Compliant Exploit of Layer 1
66 min
KinectFusion
Real-time 3D Reconstruction and Interaction Using a Moving…
54 min
Datamining for Hackers
Encrypted Traffic Mining
61 min
Time is on my Side
Exploiting Timing Side Channel Vulnerabilities on the Web
60 min
The Atari 2600 Video Computer System: The Ultimate Talk
The history, the hardware and how to write programs

53 min
Building a Distributed Satellite Ground Station Network - A Call To Arms
Hackers need satellites. Hackers need internet over…
53 min
The best of The oXcars
the greatest free/Libre culture show of all times
57 min
Hacking MFPs
Part2 - PostScript: Um, you've been hacked

59 min
Quantum of Science
How quantum information differs from classical

58 min
Counterlobbying EU institutions
How to attempt to counter the influence of industry…
107 min
Pentanews Game Show 2k11/3
42 new questions, new jokers, same concept, more fun than…
60 min
Macro dragnets: Why trawl the river when you can do the whole ocean
What happens when data collection goes awry in the 21st…

64 min
„Die Koalition setzt sich aber aktiv und ernsthaft dafür ein“
Sprachlicher Nebel in der Politik

62 min
Automatic Algorithm Invention with a GPU
Hell Yeah, it's rocket science

41 min
DC+, The Protocol
Technical defense against data retention law

49 min
Does Hacktivism Matter?
How the Btx hack changed computer law-making in Germany
62 min
The movements against state-controlled Internet in Turkey
A short account of its history and future challenges
116 min
Hacker Jeopardy
Number guessing for geeks

55 min
Introducing Osmo-GMR
Building a sniffer for the GMR satphones
51 min
BuggedPlanet
Surveillance Industry & Country's Actings

26 min
ChokePointProject - Quis custodiet ipsos custodes?
Aggregating and Visualizing (lack of) Transparancy Data in…
32 min
Antiforensik
Einführung in das Thema Antiforensik am Beispiel eines…
56 min
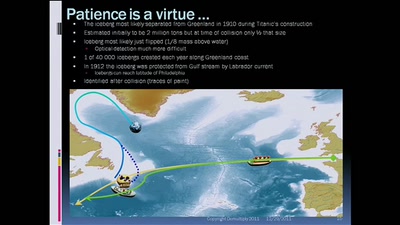
The future of cryptology: which 3 letters algorithm(s) could be our Titanic?
RMS Olympic, RMS Titanic, HMHS Britannic vs Discrete…

59 min
Echtes Netz
Kampagne für Netzneutralität

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you
75 min
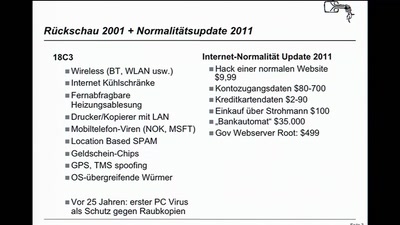
Fnord-Jahresrückblick
von Atomendlager bis Zensus
60 min
What is WhiteIT and what does it aim for?
Why you probably want to be concerned about it and similiar…

52 min
The engineering part of social engineering
Why just lying your way in won't get you anywhere

65 min
Quantified-Self and OpenBCI Neurofeedback Mind-Hacking
Transhumanism, Self-Optimization and Neurofeedback for…

51 min
Apple vs. Google Client Platforms
How you end up being the Victim.

26 min
Data Mining the Israeli Census
Insights into a publicly available registry

57 min
Politik hacken
Kleine Anleitung zur Nutzung von Sicherheitslücken…

67 min
Datenvieh oder Daten-Fee
Welchen Wert haben Trackingdaten?

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…
28 min
Ooops I hacked my PBX
Why auditing proprietary protocols matters
64 min
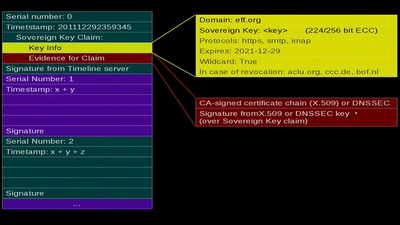
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC

70 min
"Neue Leichtigkeit"
when unconditional artistic freedom happens
100 min
NPC - Nerds’ Pissing Contest
Mein Ruby ist besser als dein urxvt!

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

43 min
CCC Camp 2011 Video Impressions
Reviving a nice summer dream
40 min
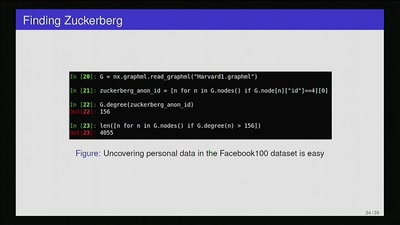
Privacy Invasion or Innovative Science?
Academia, social media data, and privacy
62 min
Cellular protocol stacks for Internet
GPRS, EDGE, UMTS, HSPA demystified

45 min
Your Disaster/Crisis/Revolution just got Pwned
Telecomix and Geeks without Bounds on Security and Crisis…
34 min
NOC Review
NOC Review about the Camp 2011 and the 28C3
52 min
From Press Freedom to the Freedom of information
Why every citizen should be concerned

128 min
Lightning Talks Day 3
Pecha Kucha Round!
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs

57 min
7 years, 400+ podcasts, and a whole lot of Frequent Flyer Miles
Lessons learned from producing a weekly independent podcast…

128 min
Der Staatstrojaner
Vom braunen Briefumschlag bis zur Publikation

56 min
Sachsen dreht frei
On- und Offline-Überwachung: Weil sie es können

59 min
Not your Grandfathers moon landing
Hell yeah, it's Rocket Science 3.1415926535897932384626!

28 min
Frag den Staat
Praktische Informationsfreiheit
57 min
Evolving custom communication protocols
Hell Yeah, it's rocket science

64 min
Can trains be hacked?
Die Technik der Eisenbahnsicherungsanlagen

59 min
Deceiving Authorship Detection
Tools to Maintain Anonymity Through Writing Style & Current…
56 min
Effective Denial of Service attacks against web application platforms
We are the 99% (CPU usage)

64 min
What is in a name?
Identity-Regimes from 1500 to the 2000s

25 min
Security Log Visualization with a Correlation Engine
What's inside your network?

54 min
The coming war on general computation
The copyright war was just the beginning

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…

55 min
Ein Mittelsmannangriff auf ein digitales Signiergerät
Bachelorarbeit Informatik Uni Kiel SS 2011

47 min
String Oriented Programming
Circumventing ASLR, DEP, and Other Guards

75 min
Fnord-Jahresrückblick
von Atomendlager bis Zensus

61 min
Electronic money: The road to Bitcoin and a glimpse forward
How the e-money systems can be made better

59 min
Almighty DNA?
Was die Tatort-Wahrheitsmaschine mit Überwachung zu tun hat

26 min