Search for person "Walter van Holst (Vrijschrift)" returned 122 results
63 min
LightKultur in Deutschland
Clubkultur oder wie modern ist unser Kulturbegriff?

25 min
GeoHealthCheck
Uptime and QoS monitor for geospatial web-services
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

44 min
Life Needs Internet
Documenting digital culture through handwritten letters

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

42 min
A world without blockchain
How (inter)national money transfers works
58 min
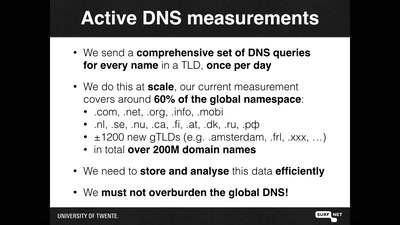
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this

27 min