Search for person "Walter van Holst"
prev
next
73 min
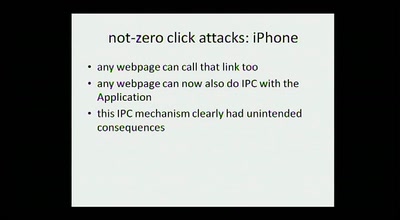
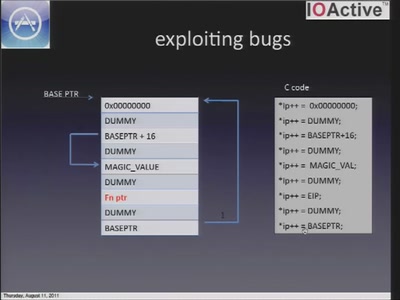
expanding the attack surface and then some
58 min
A survey of BSD kernel vulnerabilities.

38 min
oder wie man in einen Walfisch klettert, ohne ihn dabei zu…
51 min
A look at the security of 3rd party iOS applications

61 min
why clearing memory is hard.

25 min
Uptime and QoS monitor for geospatial web-services

53 min
ensuring civil rights in the digital era
prev
next

