Search for person "David Lange"
prev
next

34 min
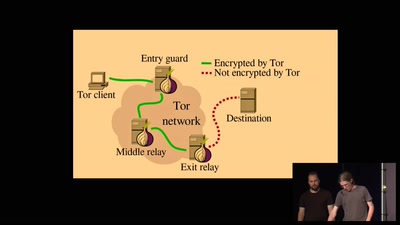
Extending capability-based security models to achieve…

58 min
An inside look at x86 CPU design
76 min
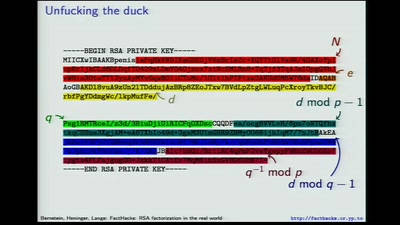
RSA factorization in the real world
65 min
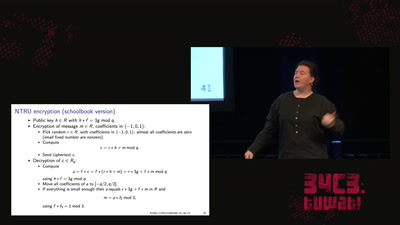
Fun with lattices in cryptography and cryptanalysis

61 min
fun(ctional) operating system and security protocol…
98 min
Essential Tips and Tricks

36 min
From eyelid blinks to speech recognition

46 min
Strong metadata protection for asynchronous messaging
65 min
Take a deep breath into pollution trickery
prev
next