58 min
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

53 min
Console Hacking 2016
PS4: PC Master Race
99 min
Fnord-Jahresrückblick
Wir helfen euch, die Fnords zu sehen!

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
59 min
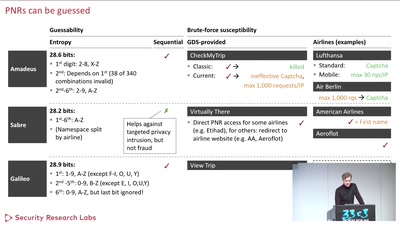
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

59 min
Die Sprache der Populisten
Wie politische "Gewissheiten" sprachlich konstruiert werden
60 min
Build your own NSA
How private companies leak your personal data into the…

42 min
A world without blockchain
How (inter)national money transfers works

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures

65 min
Nicht öffentlich.
Ein Geheimdienst als Zeuge. Szenen aus dem…

61 min
Nintendo Hacking 2016
Game Over
62 min
Machine Dreams
Dreaming Machines

60 min
Dieselgate – A year later
env stinks || exit
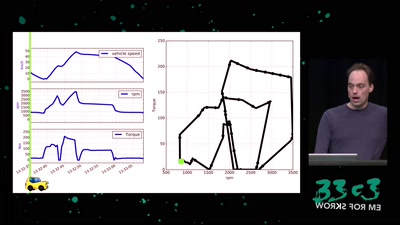
60 min
Software Defined Emissions
A hacker’s review of Dieselgate

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

60 min
Check Your Police Record!
Polizeiliche Datenbanken und was man über seinen Auskunfts-…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life
62 min
33C3 Infrastructure Review
The usual extremely factual look behind the scenes of this…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…
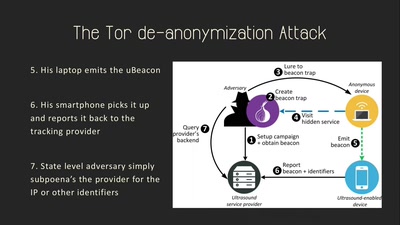
59 min
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
26 min
Eine kleine Geschichte der Parlamentsschlägerei
Schlagende Argumente, fliegende Fäuste

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
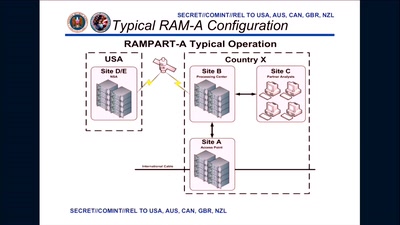
64 min
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
60 min
Es sind die kleinen Dinge im Leben
von Mikroskopen, Wahrnehmung und warum das kaum jemanden…

34 min
Bonsai Kitten waren mir lieber - Rechte Falschmeldungen in sozialen Netzwerken
Wie mit Gerüchten über Geflüchtete im Netz Stimmung gemacht…

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

57 min
Make Wi-Fi fast again
Eine kleine Einführung in den 802.11ac Standard

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

32 min
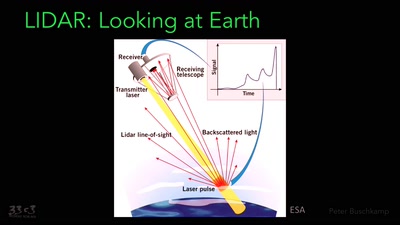
The Moon and European Space Exploration
Refocusing on the moon as a platform for future deep space…
60 min
Irren ist staatlich
10 Jahre Informationsfreiheitsgesetz

62 min
radare demystified
after 1.0

32 min
A Data Point Walks Into a Bar
How cold data can make you feel things.

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy
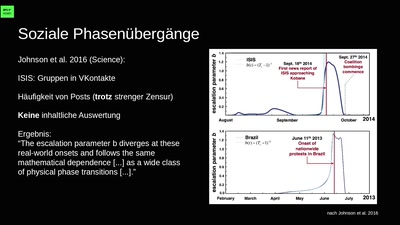
31 min
Berechnete Welt
Unsere Daten, die Zukunft und die zerstörte Demokratie

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state
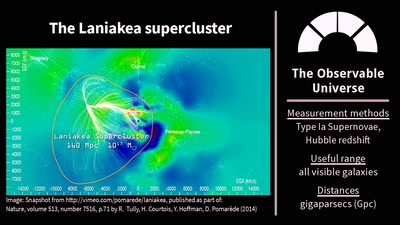
32 min
The Universe Is, Like, Seriously Huge
Stuff in Space Is Far Away – but How Do We Know?

26 min
Hacking the World
The struggle for security for all.
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now

33 min
Kampf dem Abmahnunwesen
Wider die automatisierte Rechtsdurchsetzung
60 min
Durchmarsch von Rechts
…und was wir dagegen tun können

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

60 min
Warum in die Ferne schweifen, wenn das Ausland liegt so nah?
Erinnerungen aus dem virtuellen Ausland in Frankfurt,…

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

31 min
Law Enforcement Are Hacking the Planet
How the FBI and local cops are hacking computers outside of…
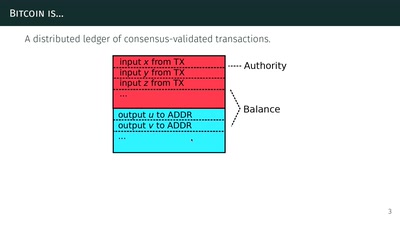
31 min
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century
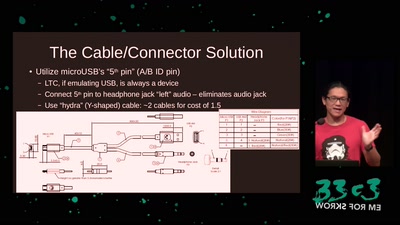
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

60 min
Von Kaffeeriechern, Abtrittanbietern und Fischbeinreißern
Berufe aus vergangenen Zeiten

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

60 min
Privatisierung der Rechtsdurchsetzung
Was der Anti-Terror-Kampf von der Urheberrechtsdurchsetzung…

33 min
Beyond Virtual and Augmented Reality
From Superhuman Sports to Amplifying Human Senses

57 min
No USB? No problem.
How to write an open source bit-bang low-speed USB stack…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

60 min
Routerzwang und Funkabschottung
Was Aktivisten davon lernen können

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

33 min
Eavesdropping on the Dark Cosmos
Dark Matter and Gravitational Waves

29 min
Edible Soft Robotics
An exploration of candy as an engineered material

109 min
Lightning Talks Day 4
Lightning Talks

31 min
The woman behind your WiFi
Hedy Lamarr: Frequency Hopping in Hollywood

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

31 min
The Clash of Digitalizations
The Devolution of Arab Men from Humans to Digital Fodder

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

60 min
Datenschutzgrundverordnung: Rechte für Menschen, Pflichten für Firmen & Chancen für uns
Schärft das Schwert der Transparenz!
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

55 min
The DROWN Attack
Breaking TLS using SSLv2

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
A Story of Discrimination and Unfairness
Prejudice in Word Embeddings

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
120 min
Lightning Talks Day 2
Lightning Talks

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…
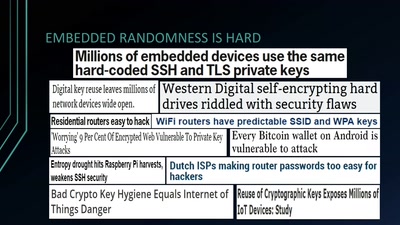
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

60 min
Hacking Reality
Mixed Reality and multi-sensory communication
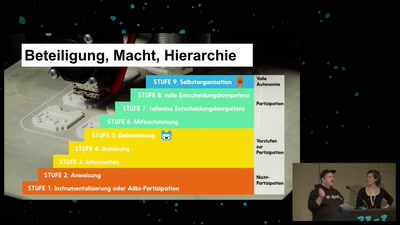
32 min
Von Alpakas, Hasenbären und Einhörnern – Über Anerkennungskultur
Wie Wertschätzung in (Tech-)Communities gelingen kann

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…
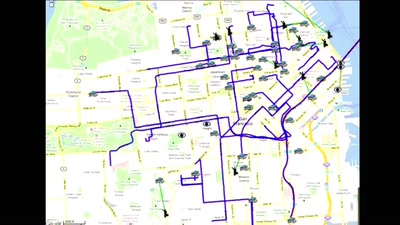
33 min
Space making/space shaping
How mapping creates space, shapes cities and our view of…
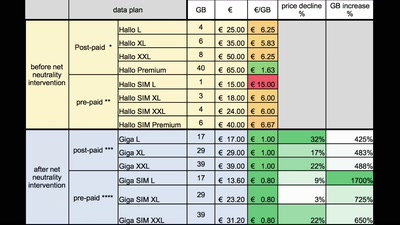
61 min
Netzpolitik in Österreich
Ein Jahresrückblick aus dem Land der Datenberge
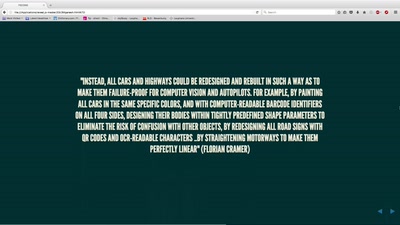
35 min
Ethics in the data society
Power and politics in the development of the driverless car
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon
31 min
Make the Internet Neutral Again
Let's put the new EU Net Neutrality rules to work
122 min
Lightning Talks Day 3
Lightning Talks
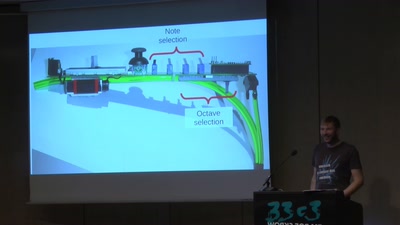
20 min
The Nibbletronic
A DIY MIDI Controller and a New UI for Wind Instruments

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

34 min
Haft für Whistleblower?
Demokratiefeindliches Strafrecht: Die Datenhehlerei gem. §…
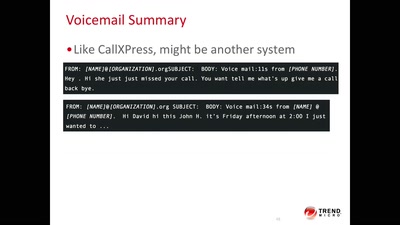
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…
28 min
Welcome to the Anthropocene?
(Did) We Accidentally a New Geological Epoch(?)

62 min
Netzpolitik in der Schweiz 2016
Grundrechte per Volksentscheid versenken
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone

30 min
Syrian Archive
Preserving documentation of human rights violations

29 min